Manage MySQL
Database Security:
Best Practices & Tips
MySQL is one of the biggest, most popular database management systems to ever see the light of day, and with so much involved data and so many MySQL-based consumer applications, it is absolutely essential to keep it all safe from any sort of accidental leakage or malicious intent. Here are some best practices and tips that will help you shield your MySQL databases from it all.
Below we cover the essentials of database security in MySQL, including the following:
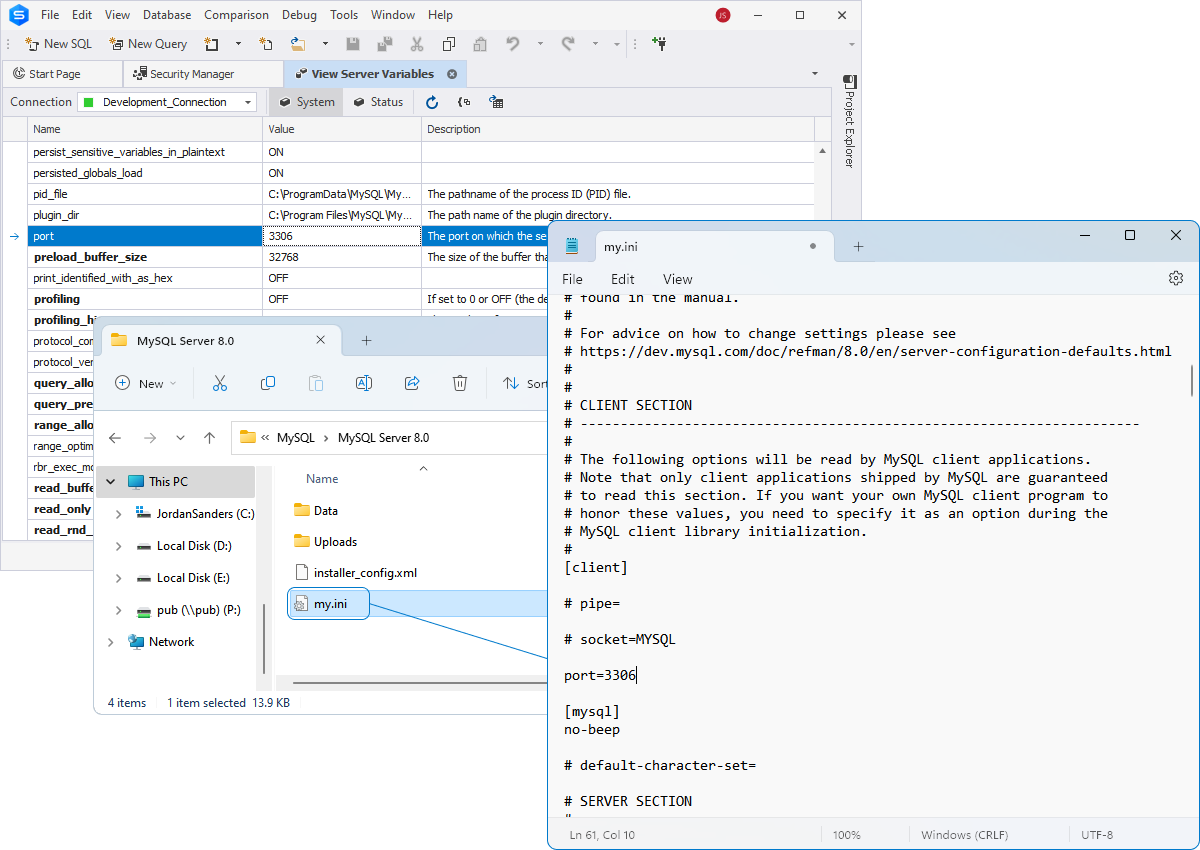
- Change the default MySQL port
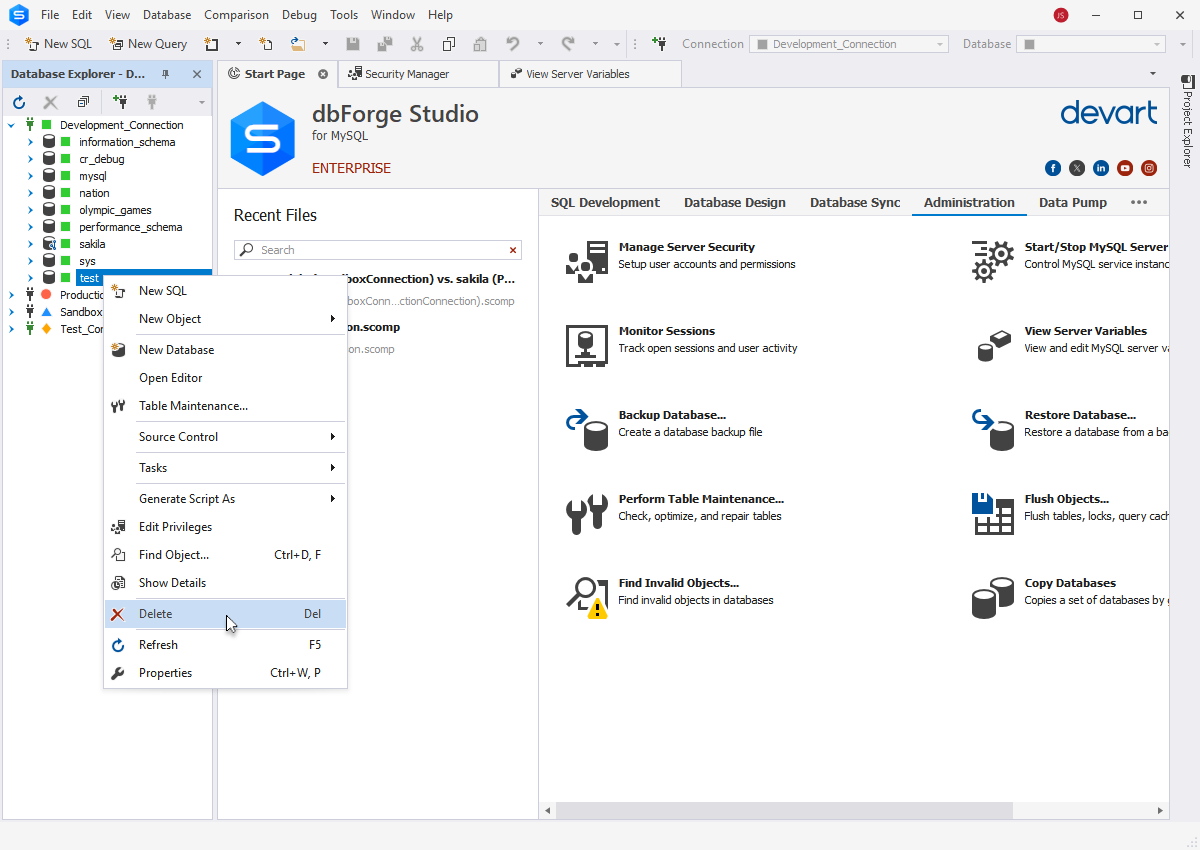
- Drop test databases
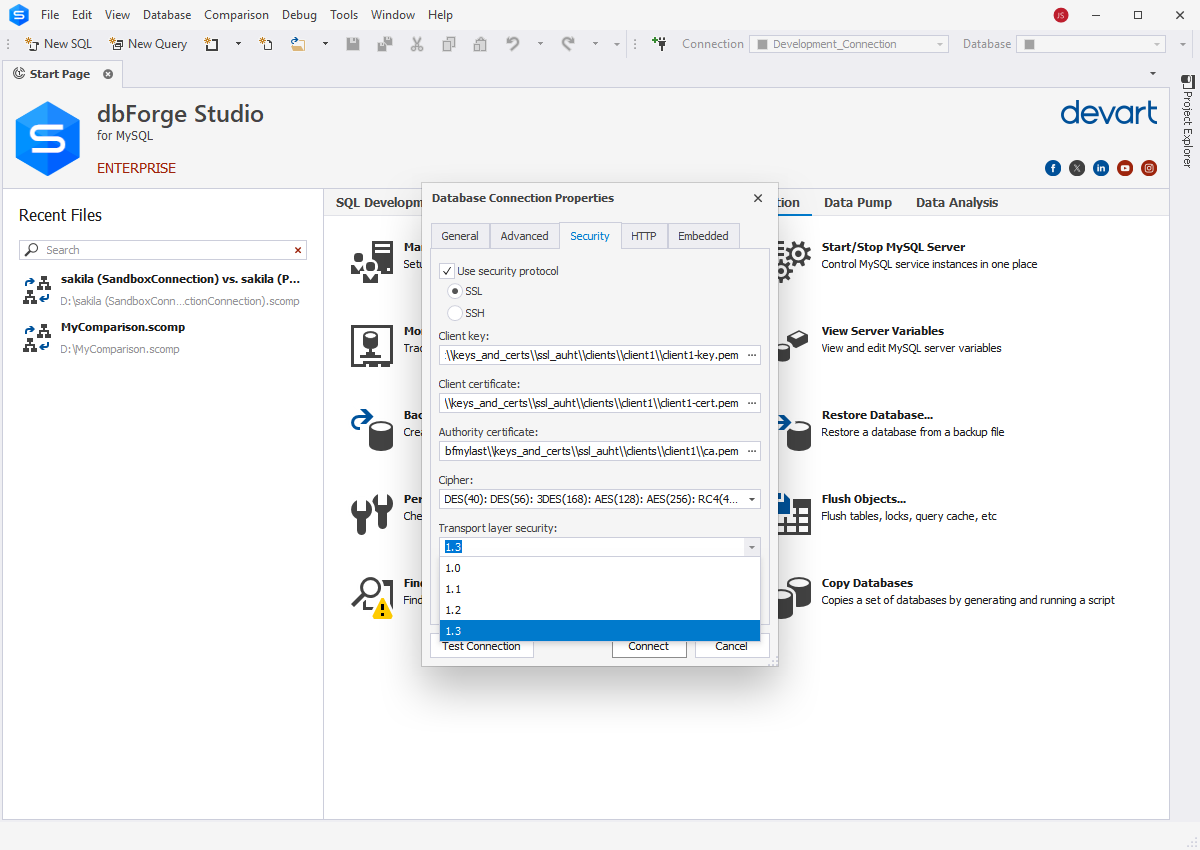
- Set up SSL connection
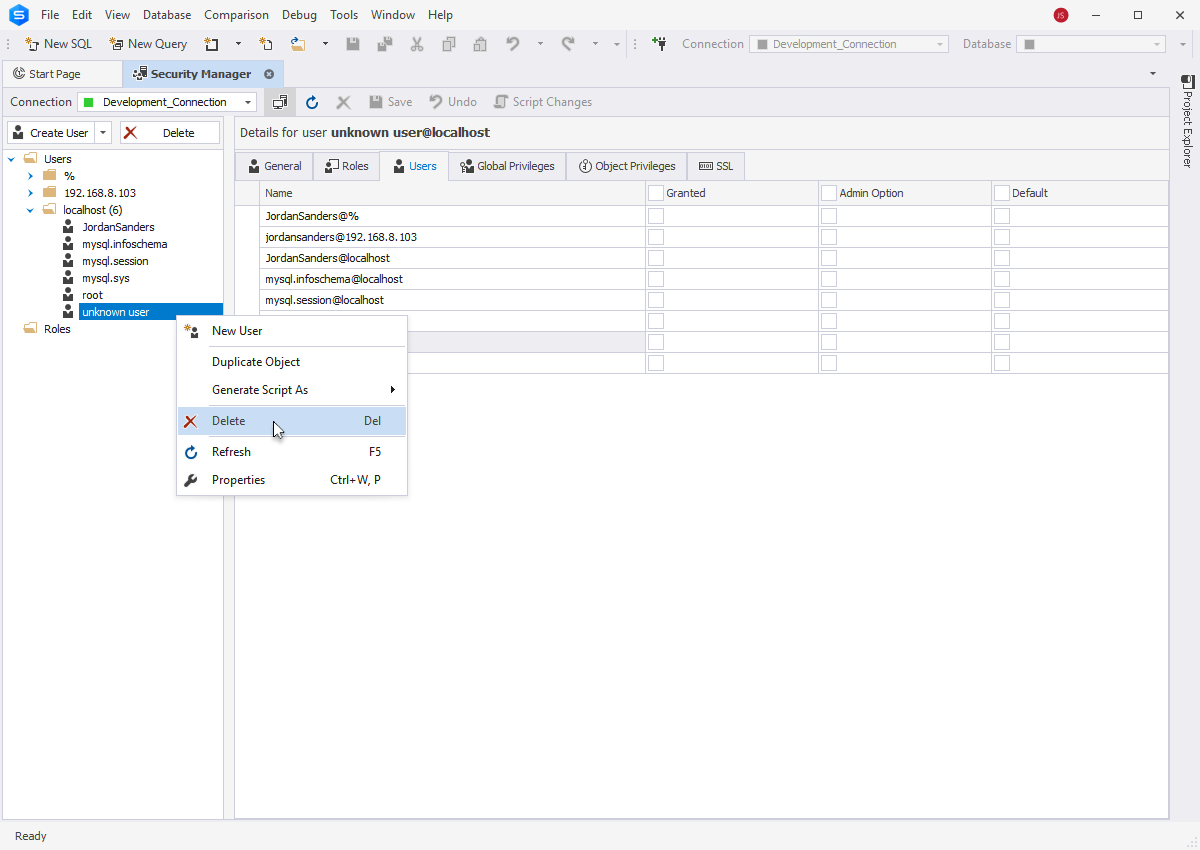
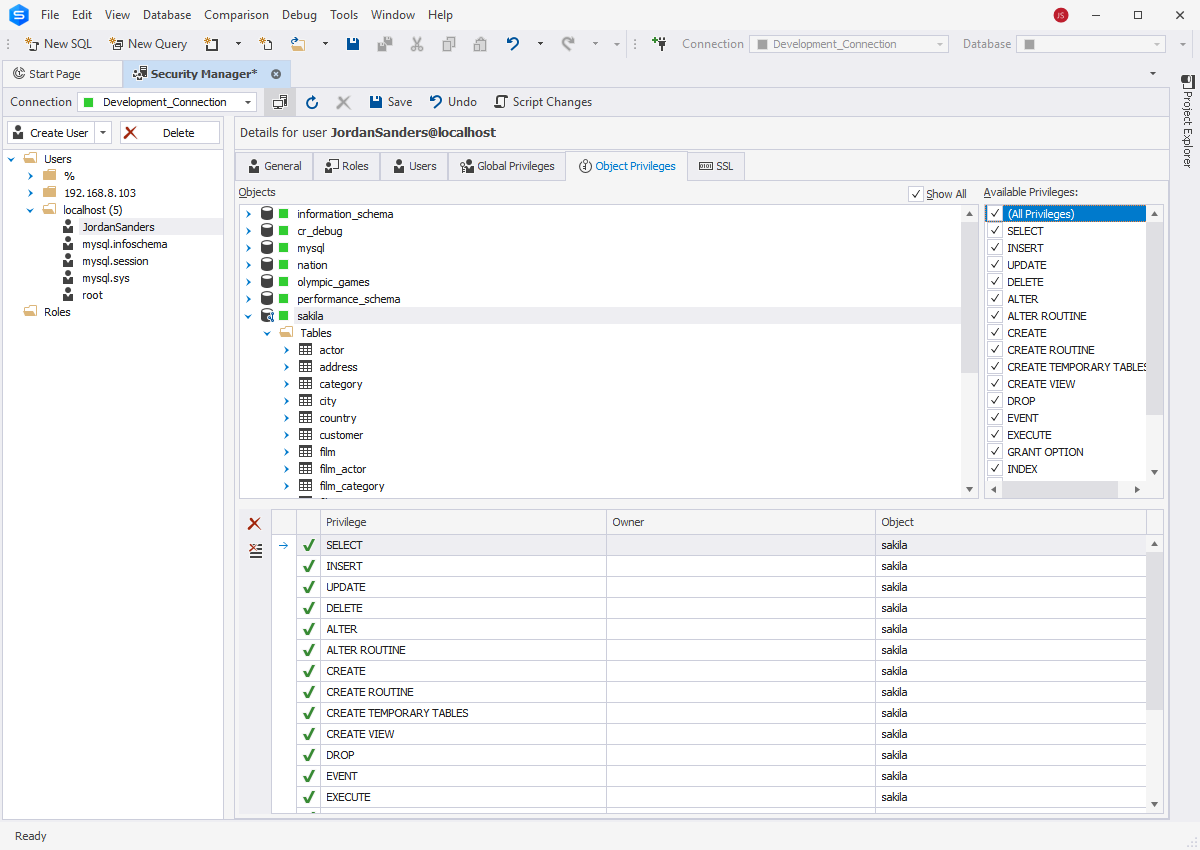
- Remove all anonymous users
- Avoid running MySQL with root-level privileges
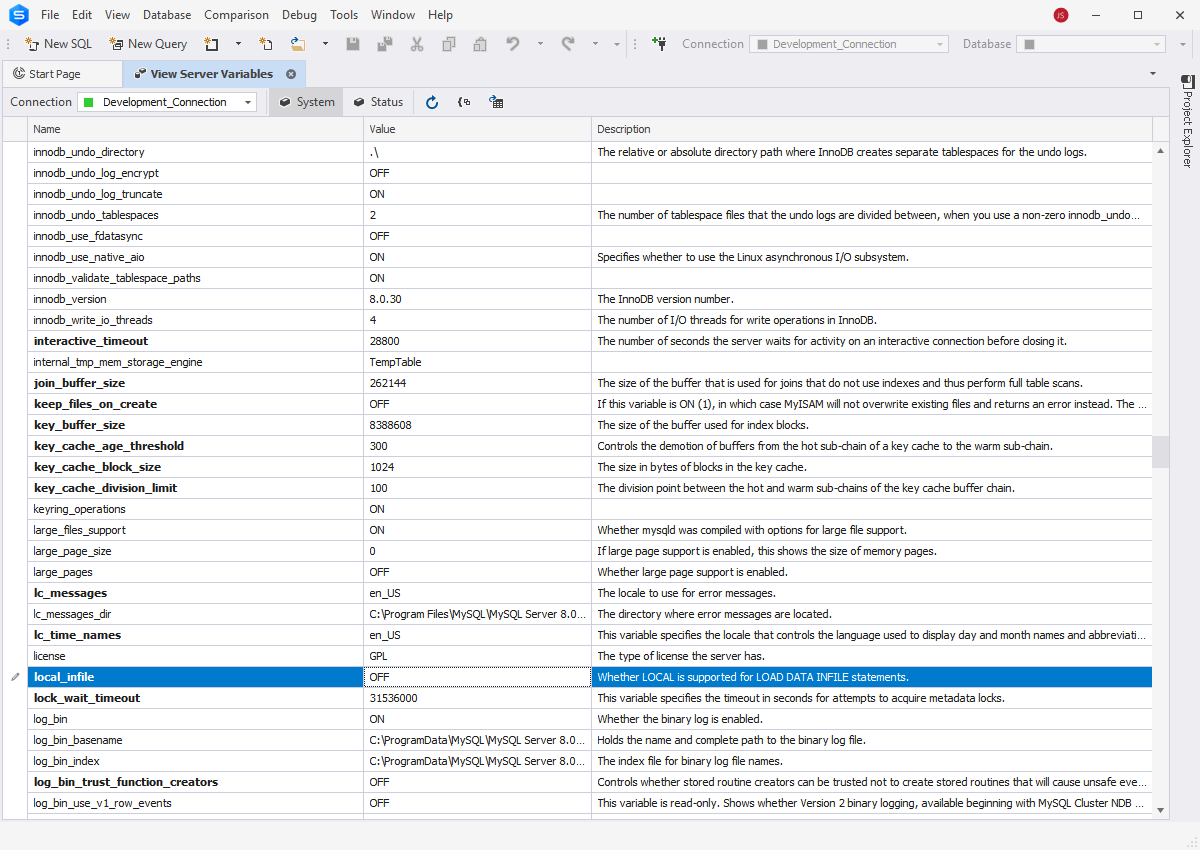
- Disable the LOAD DATA LOCAL INFILE command
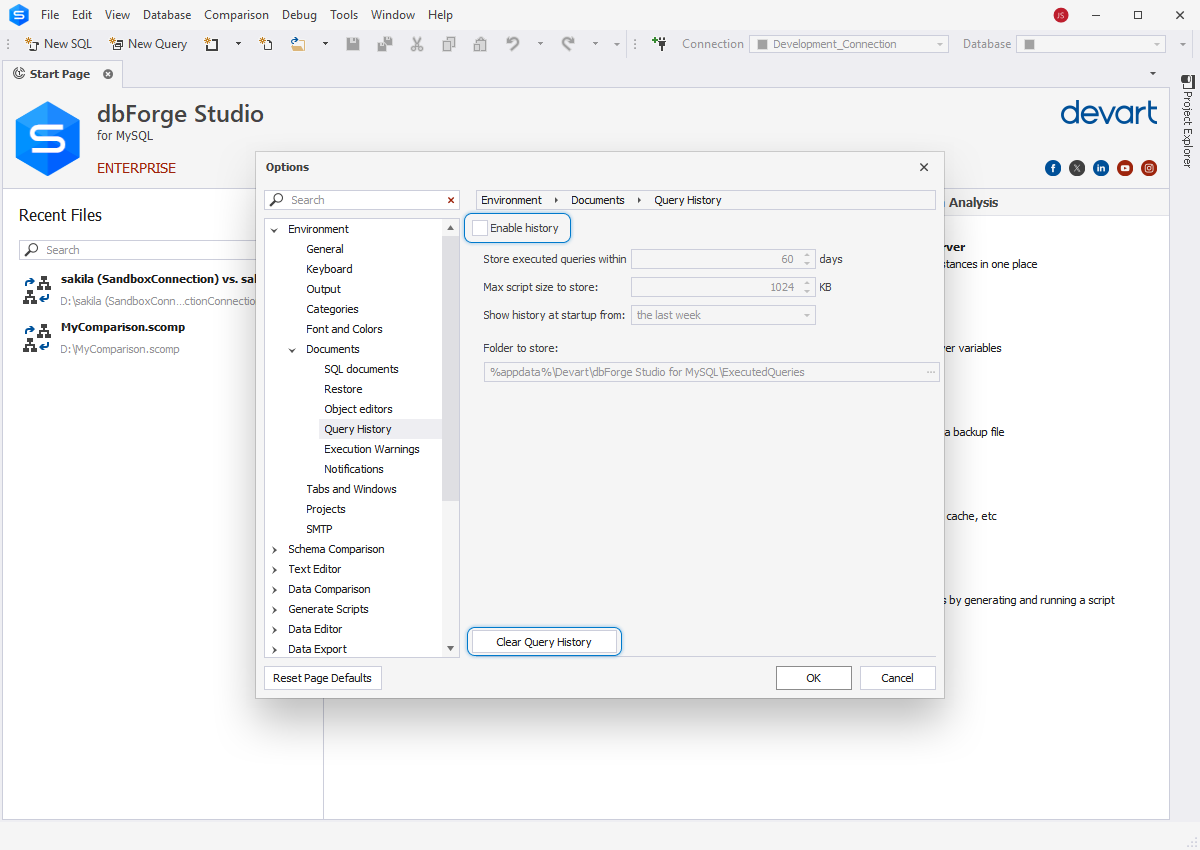
- Disable and remove MySQL history logs
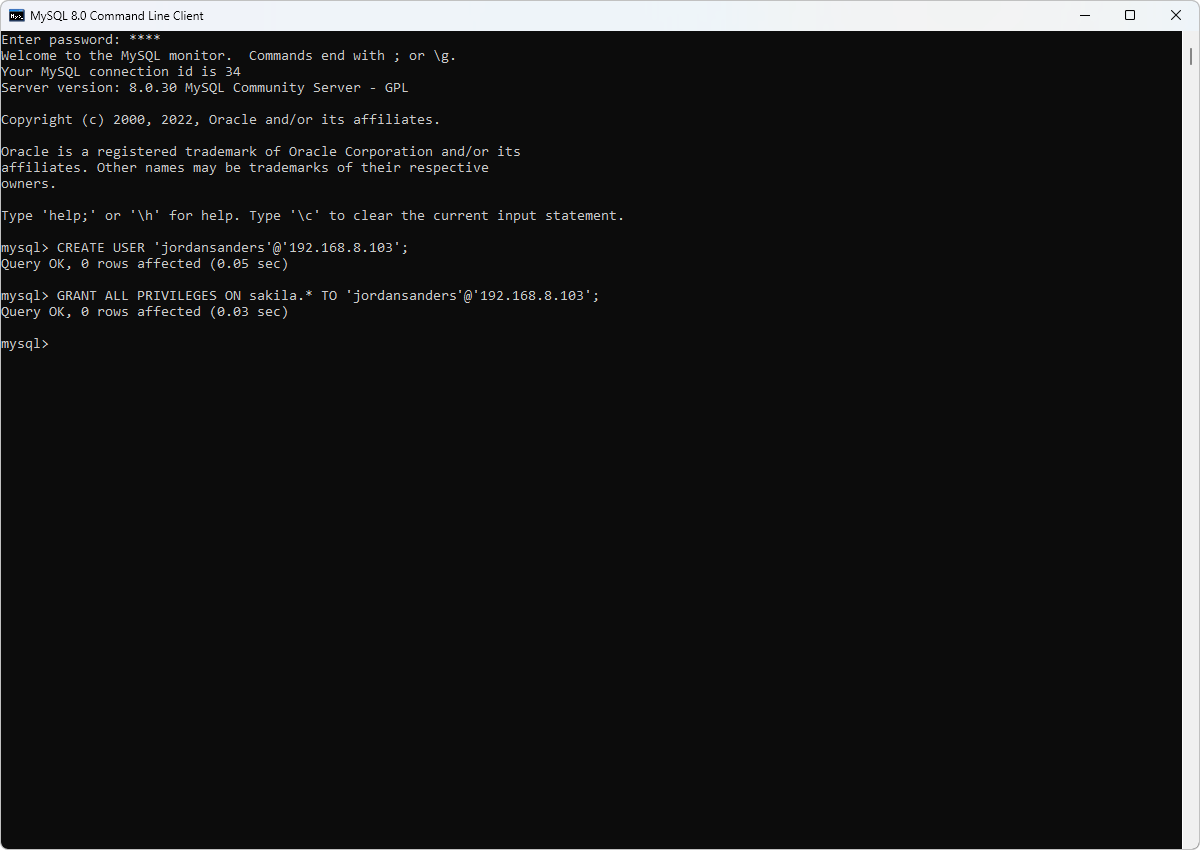
- Configure allowed IP addresses and hostnames
- Row-level security in MySQL explained: Why it matters